GitHub
You can configure Okteto to give your developers access to private GitHub repositories.
There are several reasons for considering this approach including:
- Your users can select a repo from a list, instead of having to type the full repository URL.
- Give everyone on your cluster read-only access to private repositories.
- Control access to Okteto and the repositories at the Organization level, or per repository.
- The pipelines use an app-scoped token, instead of a shared ssh key.
Configure your GitHub integration
- Self-Hosted
- SaaS
Follow the guide to configure the GitHub integration.
If your instance is hosted by Okteto, the GitHub integration is enabled by default.
Adding or removing private repositories
You can update or revoke the permissions over your private repositories or organizations by going to the Integrations section in the Settings page of your Okteto instance.
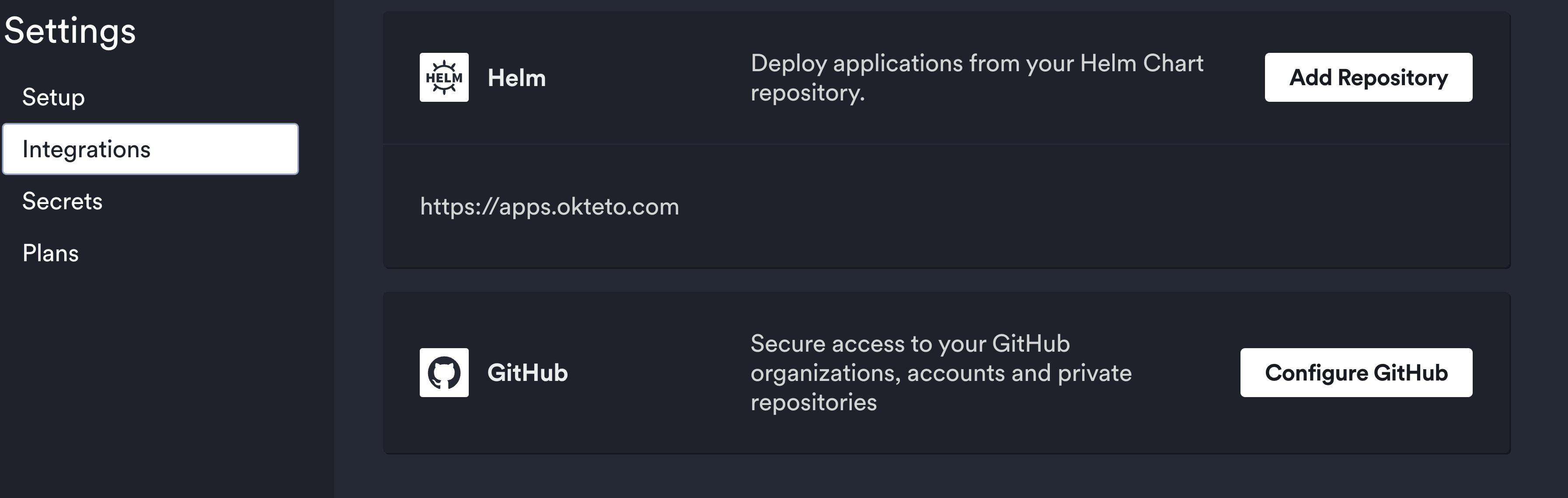
Click on the Configure GitHub button to add or remove repositories. This will open a configuration dialog from GitHub. From there, you'll be able to add or remove repositories from any organization you belong to.
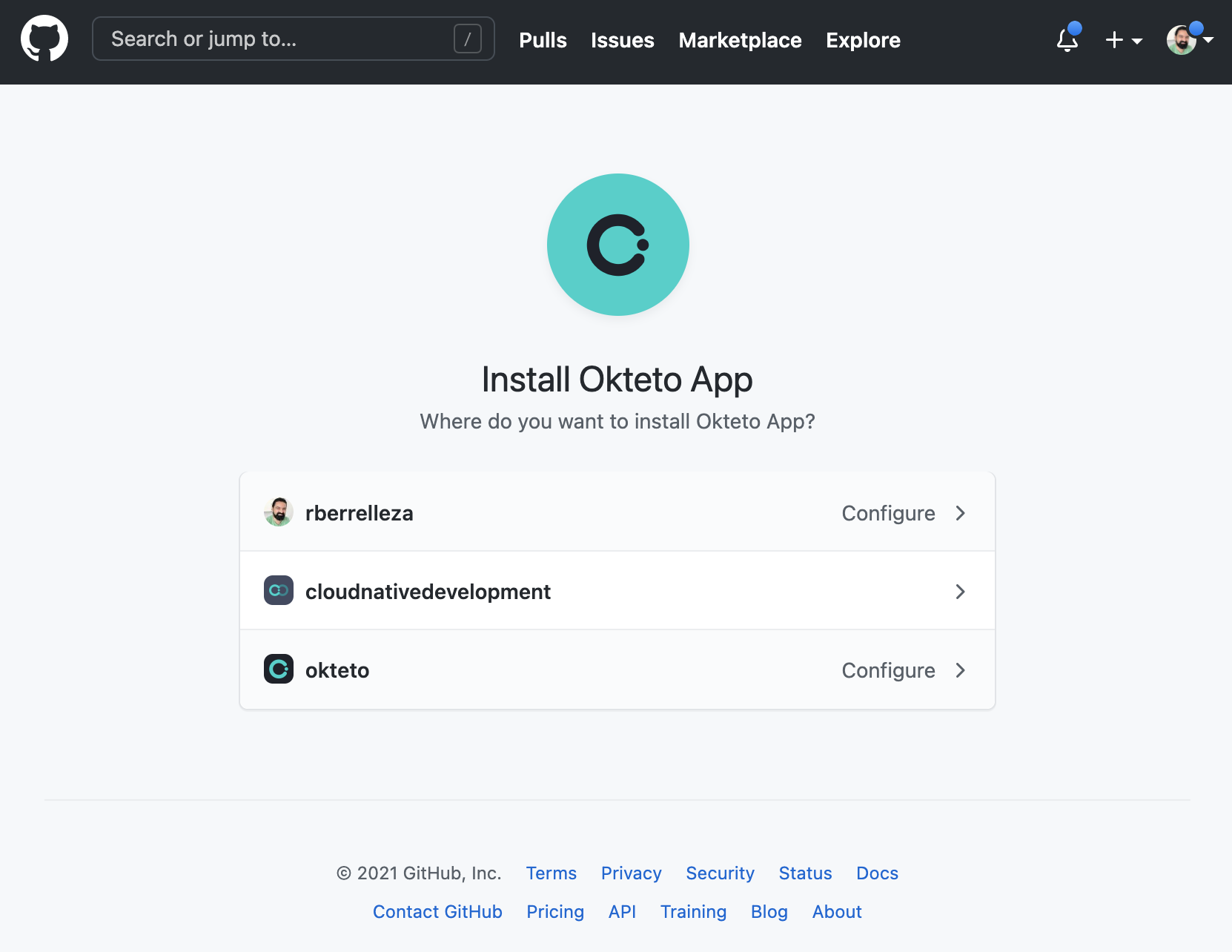
If you select repositories from a different organization (or user account) than the one you used to create the GitHub Application, GitHub will prompt you to install the application in the GitHub organization. Only organization administrators can complete this action.
GitHub org administrators
If you're an administrator, you can grant team members access to your organization's repositories. Please note, even if you grant Okteto permission to all of your organization's repositories, each developer will only have access to those repositories that they are able to access through GitHub. This allows you to maintain security, and ensure that only those authorized to access code may do so.